
This is some text inside of a div block.
This is some text inside of a div block.
Cyber threats are growing more sophisticated every year, and businesses can no longer rely solely on firewalls or basic antivirus software to protect their data. With the rise of cloud services, remote work, and flexible devices, security needs to adapt to a modern, dynamic workplace. One of the most effective tools to achieve this is Conditional Access.
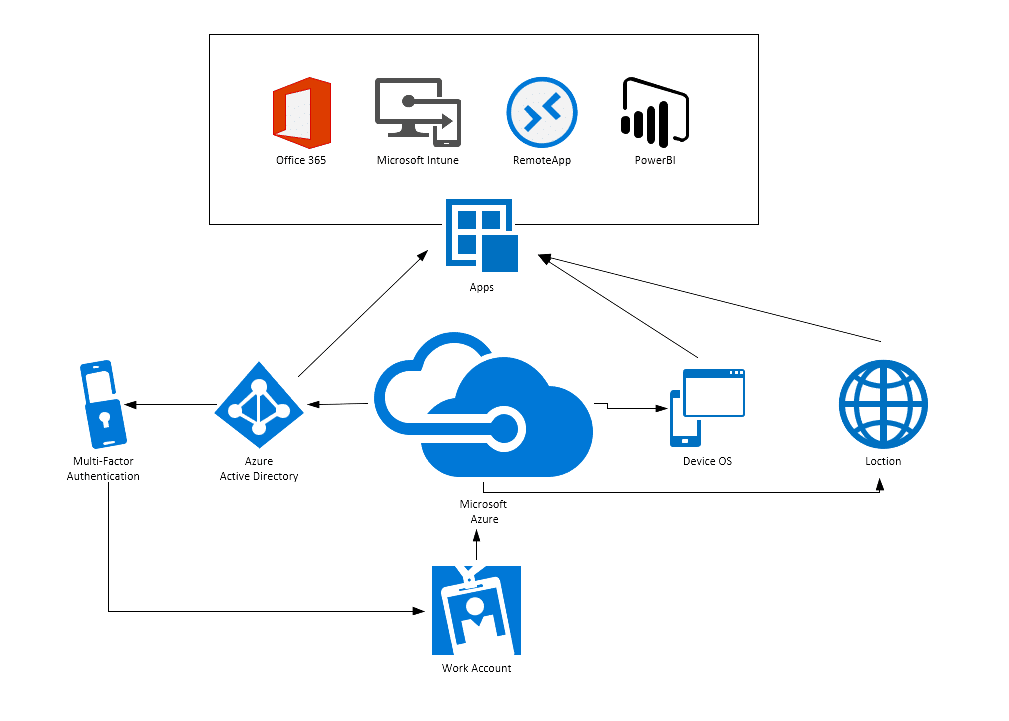
In simple terms, Conditional Access is a security feature that allows organisations to control access to applications, systems, and data based on specific conditions. It’s like having a digital security guard that checks who is trying to enter, what device they’re using, and where they’re coming from—before granting access.
If your business uses Microsoft 365, Azure Active Directory, or other identity management tools, Conditional Access can drastically reduce the risk of data breaches while giving employees a smooth and secure user experience.
Conditional Access is a security mechanism that applies rules—known as policies—to decide whether a user should be granted access to a resource. These rules can take into account:
If the access request meets the conditions, the user gets in. If not, additional verification—such as Multi-Factor Authentication (MFA)—may be required, or access may be blocked altogether.
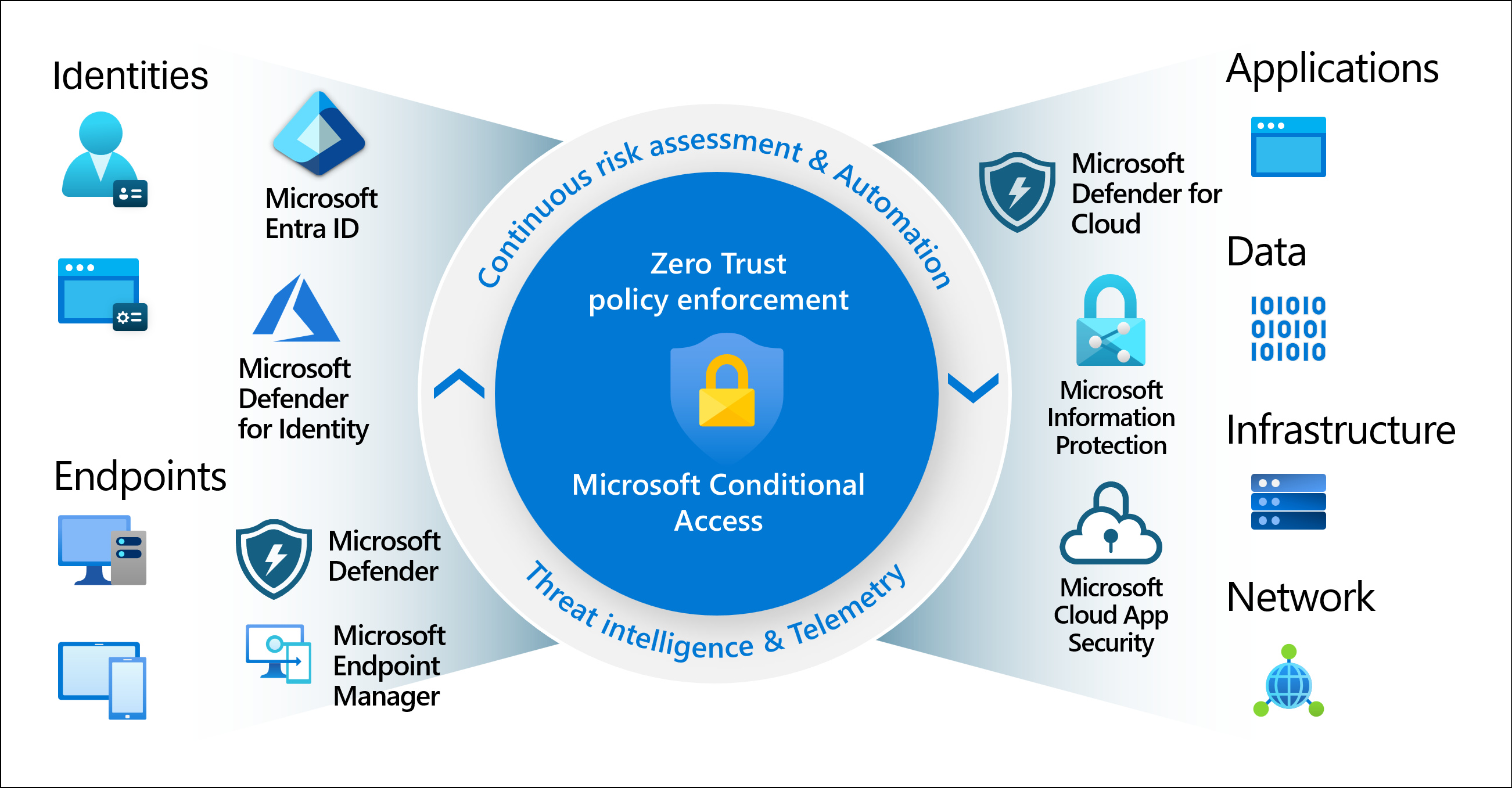
The traditional security model assumed that anyone inside the office network could be trusted. But with employees working from home, travelling, or using public Wi-Fi, the “castle and moat” approach no longer works. Conditional Access enforces security no matter where your users are.
Most breaches occur because an attacker gained access to legitimate login credentials. With Conditional Access, simply having the username and password isn’t enough—they must also meet security conditions, such as passing MFA or signing in from a compliant device.
Industries like finance, healthcare, and legal services often have strict compliance requirements. Conditional Access helps meet these by ensuring sensitive data is only accessed under approved circumstances.
Imagine Sarah, a project manager, trying to access her company’s Microsoft Teams while on holiday abroad. Conditional Access policies might detect:
Instead of granting immediate access, Conditional Access could:
This dynamic approach keeps productivity flowing while keeping threats out.
Here are some of the most useful features businesses can take advantage of:
Conditional Access creates a balance—security measures only trigger when needed, so employees aren’t constantly disrupted.
Even if a hacker steals a username and password, they can’t log in unless they also meet your access conditions.
Every business is different. You can set policies that align with your risk appetite, industry compliance needs, and working style.
Admins can monitor sign-in attempts, blocked access, and suspicious behaviour—all from a central dashboard.
Here are some real-world examples of Conditional Access policies businesses often set up:

If you’re using Microsoft 365 Business Premium, Azure Active Directory Premium P1/P2, or Enterprise licenses, Conditional Access is already available to you. Implementation typically follows these steps:
Conditional Access is no longer a “nice-to-have”—it’s a must-have security layer for modern businesses. By allowing access only under trusted conditions, it protects sensitive data, meets compliance requirements, and gives you peace of mind in an increasingly complex digital world.
Whether you have a small team or a large enterprise, implementing Conditional Access can be one of the smartest cybersecurity investments you make this year.
If you’re ready to secure your business with Conditional Access, our IT experts can help you plan, configure, and maintain policies that keep your data safe without slowing down your team.