Alert: A clever new type of ransomware attack
Alert: A Clever New Type of Ransomware Attack Is On the Rise - What Your Business Needs to Know
In the ever-evolving world of cybercrime, ransomware continues to be one of the most damaging threats facing businesses today. But now, cybercriminals have stepped up their game.
A clever new type of ransomware attack has recently been discovered — and it’s catching many businesses off guard. This sophisticated threat uses tactics that bypass traditional security tools and exploit human error, making it more dangerous than ever.
If your business relies on digital infrastructure (and whose doesn’t?), understanding how this new attack works — and how to defend against it — is essential.
🔐 What Is Ransomware and How Does It Typically Work?
Ransomware is a type of malicious software (malware) that encrypts files on a device or network. Once the files are locked, attackers demand a ransom — usually in cryptocurrency — in exchange for the decryption key.
Traditional ransomware attacks usually start through:
- Phishing emails
- Infected software downloads
- Remote Desktop Protocol (RDP) vulnerabilities
But the new wave of ransomware goes far beyond these old tricks…

🧠 What Makes This New Ransomware "Clever"?
This newly observed ransomware strain is stealthy, highly targeted, and more manipulative than its predecessors. Here’s what makes it so different:
1. Double Extortion Technique
Not only do attackers encrypt your files, but they also steal sensitive data first. Then, they threaten to publish or sell it unless you pay up. This double threat increases the pressure to give in to demands.
2. Living Off the Land (LotL) Attacks
Instead of dropping new malware files that can be detected by antivirus software, attackers use legitimate system tools already installed on your devices — like PowerShell or Windows Management Instrumentation (WMI) — to carry out the attack. This makes detection extremely difficult.
3. Targeted Reconnaissance
Cybercriminals spend time inside your network before deploying the ransomware. They study your systems, identify key files, and even disable backup solutions so recovery becomes harder.
4. Timing Is Everything
Attackers now launch ransomware outside of normal business hours, such as weekends or holidays, when IT staff are less likely to notice or respond quickly.
🧪 Real-World Example: How One Business Was Tricked
A medium-sized UK law firm recently fell victim to this type of ransomware. The attack began with a very convincing phishing email from a supplier they’d worked with. It contained no malicious attachments — just a link to a shared file.
Once the file was opened, the attacker had access to the network, monitored activity for days, and eventually launched the ransomware on a Saturday night. By Monday morning, the firm was locked out of every system — and sensitive client data had been exfiltrated.
The ransom? Over £150,000 in Bitcoin.
🛡️ How to Protect Your Business from This Ransomware Threat
✅ 1. Invest in Advanced Threat Detection
Standard antivirus isn’t enough anymore. You need a next-generation endpoint detection and response (EDR) solution that monitors behaviour, not just files.
Tip: Consider Microsoft Defender for Endpoint or SentinelOne as part of your security stack.
✅ 2. Implement Zero Trust Security
Don’t trust anyone by default — even inside your network. Apply Zero Trust principles:
- Multi-Factor Authentication (MFA) everywhere
- Network segmentation
- Role-based access control
✅ 3. Regularly Back Up Your Data — and Test It
Keep secure, off-site backups that are separated from your main network. And just as importantly, test your backups regularly to ensure they actually work in a disaster recovery scenario.
✅ 4. Educate Your Employees
Many ransomware attacks start with a single click. Regular cybersecurity awareness training helps staff identify phishing emails and other threats before it’s too late.
Need help training your staff? Ask us about our phishing simulations and awareness workshops.
✅ 5. Keep Software and Systems Updated
Always apply the latest security patches and updates to your operating systems, firewalls, VPNs, and other tools. Vulnerabilities are an easy entry point for ransomware.
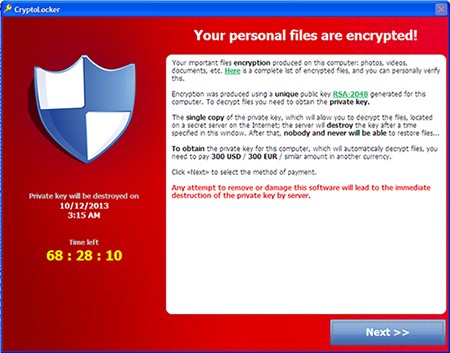
🚨 What to Do If You’re Under Attack
If you suspect your business has been targeted by this kind of ransomware:
- Disconnect affected systems from your network immediately
- Do not pay the ransom – it funds criminal activity and doesn’t guarantee you’ll get your data back
- Report the incident to the UK's National Cyber Security Centre (NCSC)
- Contact a cybersecurity specialist (like us) immediately for incident response and containment
👨💻 Don’t Wait Until It’s Too Late
Ransomware attacks are growing more sophisticated, frequent, and financially devastating. Even small businesses are now prime targets.
At Sonar IT, we help businesses across London and Essex improve their cyber resilience with:
- Advanced endpoint protection
- Ransomware-proof backup strategies
- Employee training
- 24/7 monitoring and response
- Microsoft 365 security solutions
🛡️ Let’s Fortify Your Defences
Worried your current cybersecurity setup won’t stand up to the latest ransomware threats?
📞 Call us on 0203 011 0805
📧 Email: ontheradar@sonarit.co.uk
Or visit our Cybersecurity Services page to see how we can help protect your business from emerging threats.
.svg)
%2520(1).avif)





